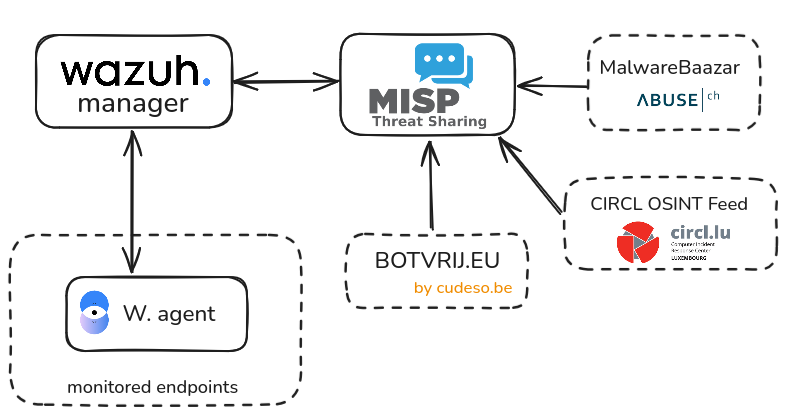
FlowIntel 3.0.0 released and MISP integration
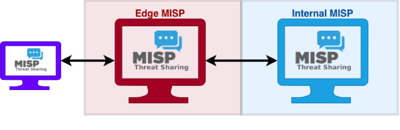
FlowIntel & MISP
FlowIntel in a Nutshell
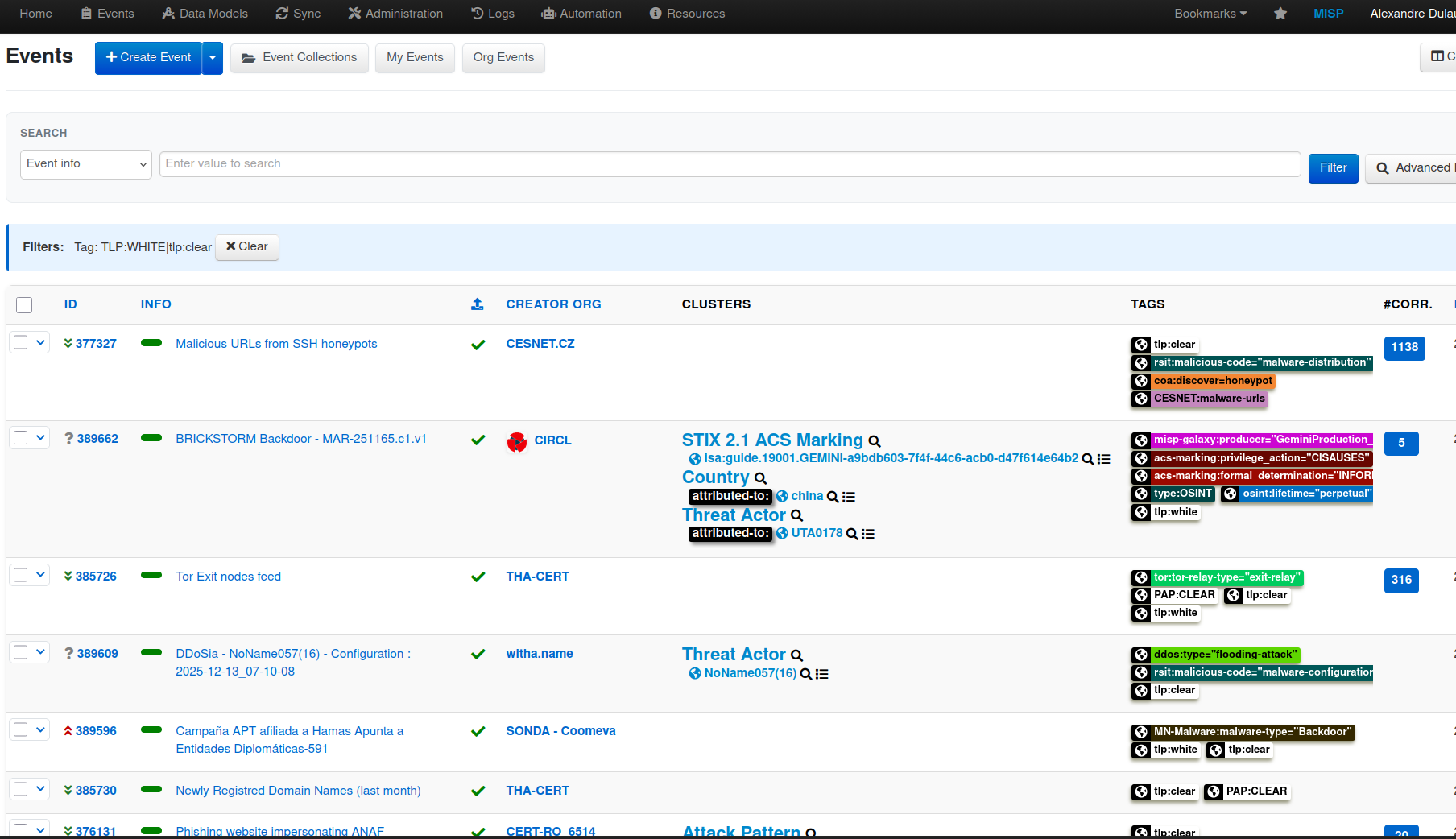
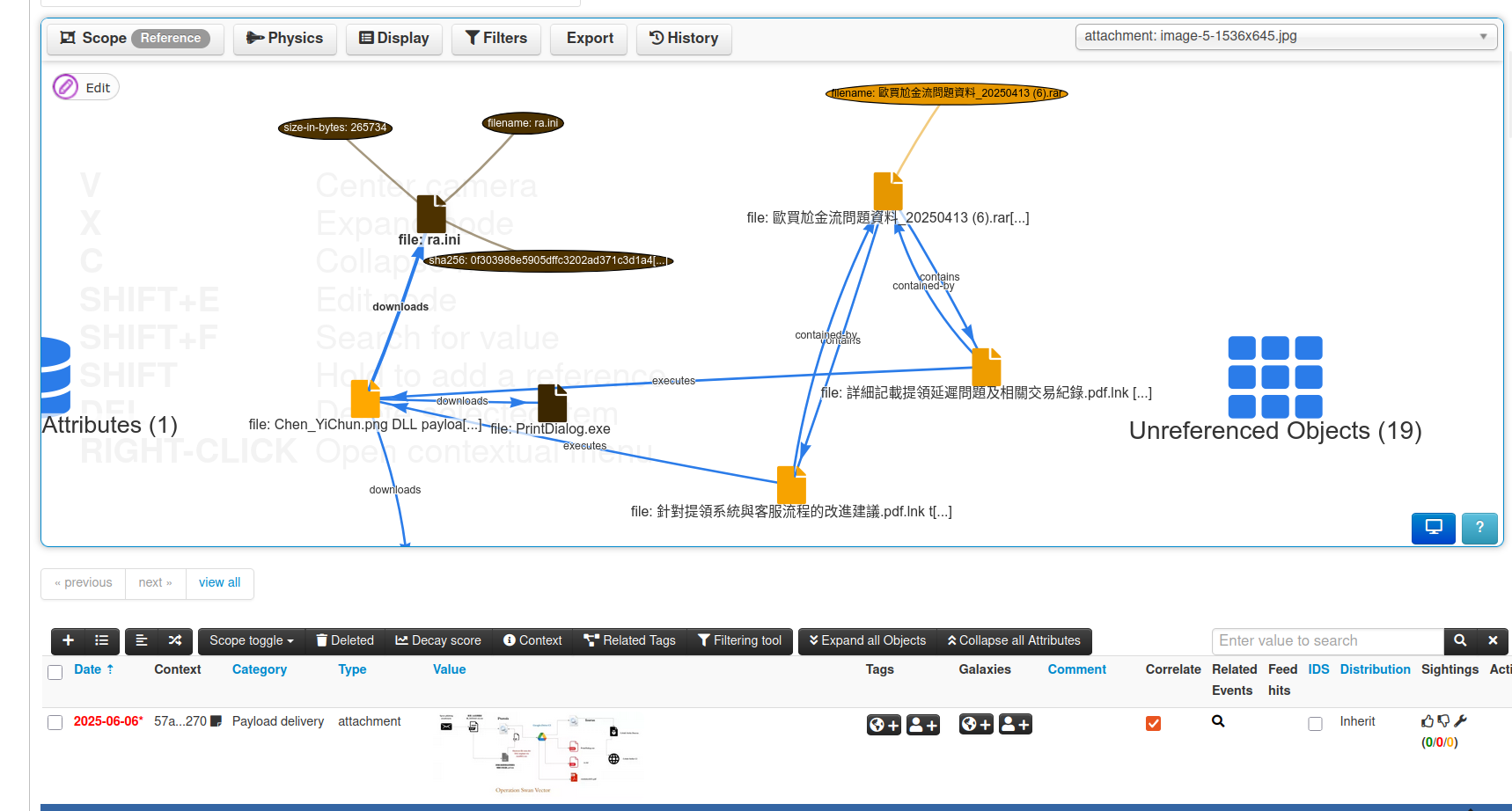
FlowIntel is an open-source platform built for handling security investigations in a structured way. It combines case management, task tracking, documentation, and collaboration in one place.